TCP encryption
DEDITEC ETH modules secure the data transmission in the same way as a classic cipher: With the help of an algorithm - a tap-proof TCP communication - readable characters are converted into unreadable characters within the DEDITEC-delib.dll before the data is passed on. The data can only be read again by decrypting it when it is read out. The encryption algorithm is stored in the software and, if password-protected, cannot be viewed - comparable to the end-to-end data encryption of modern mail programs or messaging apps.
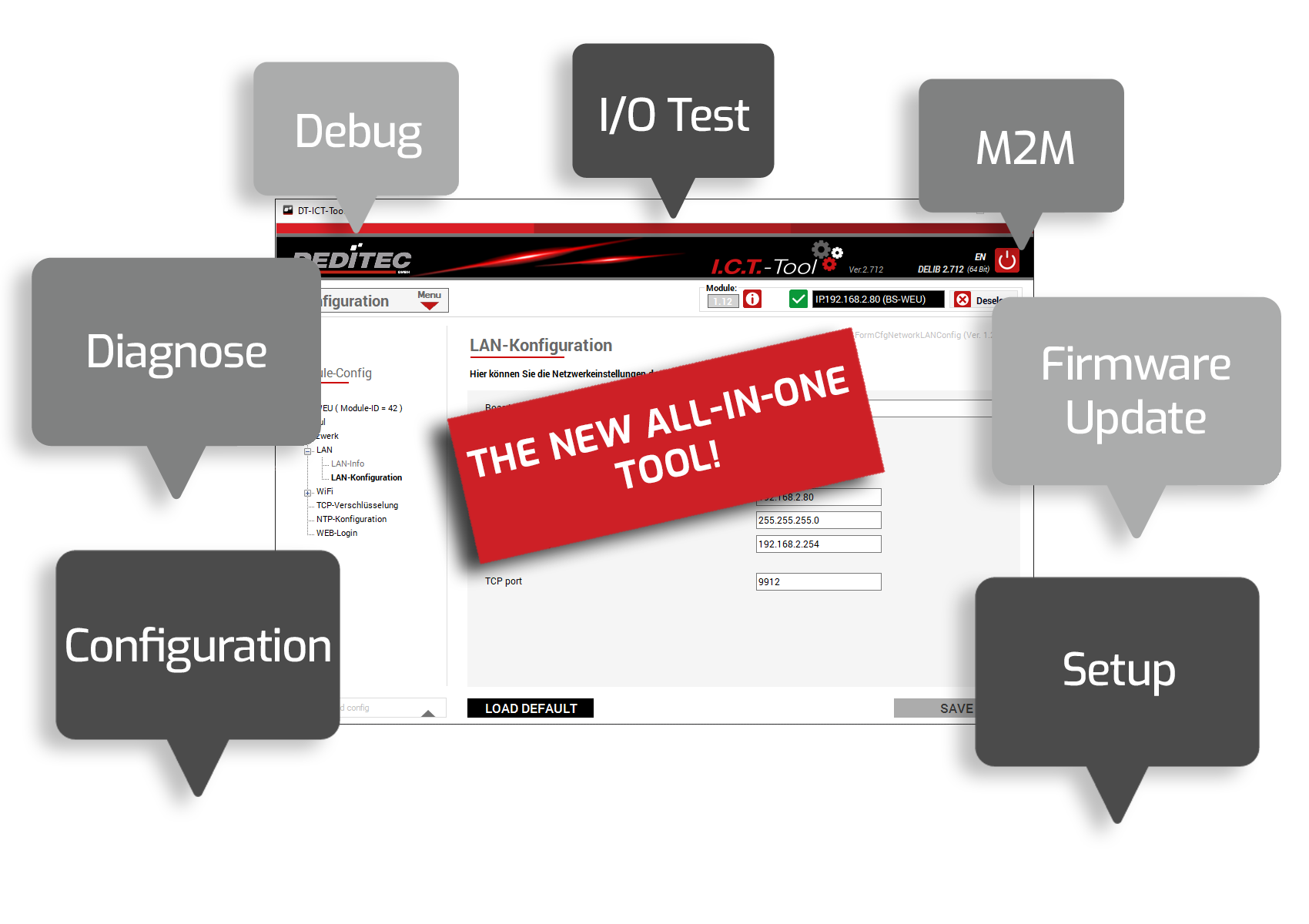
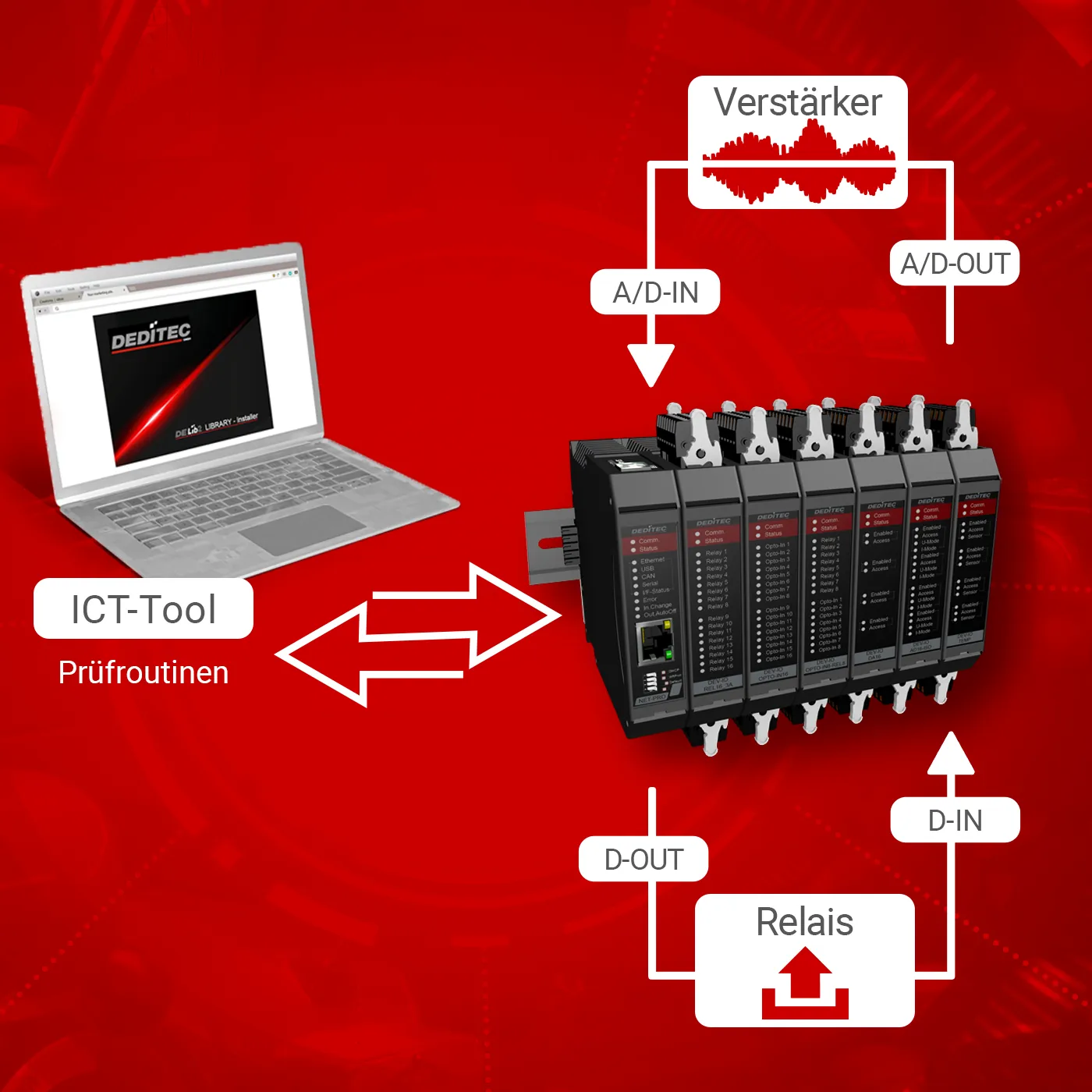
TCP communication between the user and module is secured for the modules with the help of a password. In order to write the password securely to the module, in addition to direct configuration via USB, it is also possible to encrypt the password in the ICT tool via Ethernet using the temporary admin mode.
The encryption types for ETH modules can be configured in four modes so that the security can be controlled in stages. From admin, temp admin and user encryption mode to unencrypted transmission, the option of assigning a password can be configured. This enables a wide range of applications, even in large systems with different user levels.
Encryption on the DEDITEC ETH module
With numerous configuration options and different levels of access to the encryption, the DEDITEC ETH modules are prepared for a wide range of applications and can also be used in large systems with complex protection.
In admin mode, full access to I/Os and module configuration is granted; TCP transmission is encrypted. When configuring in temporary admin mode, switches or buttons must be physically operated directly on the board to ensure that no unauthorized person can carry out this configuration. With user encryption, the transmission is encrypted and the user can access I/Os but cannot modify the module configuration. Only in the lowest security level “Unencrypted” can the module be accessed unencrypted (without a password). However, this type of access can also be prohibited in the configuration to protect the module.
All-round talents with coding protection: The different application and configuration modes of Encryption make the ETH modules from DEDITEC usable and ready for encryption in a wide variety of areas.
Security measures for ETH modules
Write protection
With DIP switch 2, you can deactivate access via the Ethernet or USB interface to the module configuration memory with write protection. DIP-2 on = write protection active DIP-2 off = write protection deactivated.
TCP encryption
You can use the ICT-Tool to encrypt communication via TCP. Partial or full access to the module configuration memory can also be set using the admin and user protocols.
Encryption types
- Unencrypted: The module can be accessed unencrypted
- User encryption: TCP transmission is encrypted. The I/Os can be accessed, but no changes can be made to the module configuration
- Admin encryption: TCP transmission is encrypted. Full access to I/Os and module configuration
- Temp Admin: Temporary encryption mode to transfer the set password to the module in encrypted form